Huawie S3700 supports port mirroring. The details are as follows:
A maximum of four observing ports can be configured on an S3700. Packets from
multiple ports can be mirrored to the same observing port. You can mirror incoming
packets, outgoing packets, or both to an observing port.
The S3700 supports Remote Switched Port Analyzer (RSPAN). That is, the observing
port and mirrored port can be located on different switches. This facilitates remote
device management.
The S3700 such as S3700-52P-EI-48S-AC supports traffic mirroring. A maximum of four observing ports can be configured on an S3700. Flows can be mirrored from multiple ports to the same
observing port. Flows to be mirrored are determined by the traffic classification rule.
Thunder-link.com supply original new Huawei optical network equipments, offering all series Huawei OSN, Huawei OLT, Huawei Switch, Huawei SDH, Huawei WDM,Huawei ONT products with good quality and one year warranty. Welcome visit our website:www.thunder-link.com or send e-mail:Sales@thunder-link.com
Thursday, June 29, 2017
Configuring a GPON ONT Capacity Profile (Distributed Mode)
A GPON ONT capability profile identifies the actual capability of a GPON ONU. After an ONT is added and bound to a Huawei GPON ONT capability profile, the ONU carries the corresponding services according to parameters configured in the capability profile.
Context
All GPON ONUs must be bound to the GPON ONT capability profile. Specify the ONT capability profile when running the ont add command to add an ONU offline or running the ont confirm command to confirm an automatically discovered ONU.
Currently, the system provides seven default ONT capability profiles that are solidified in the system. The default profiles cannot be modified. The default profile IDs range from 1-7. The reserved ONT capability profile IDs are 8-16.
The contents of the capability profile restrict the port number that is used in commands for GEM port mapping, T-CONT/PQ mapping, and the ONT VLAN management.
The ONT capability profile must be configured according to the actual capability of the ONU. Different the capability profile parameters vary according to different ONUs.
Procedure
Step 1 Run the ont-profile add command to configure an ONT HG8546M capability profile.
Step 2 Run the display ont-profile command to query the ONT capability profile.
Context
All GPON ONUs must be bound to the GPON ONT capability profile. Specify the ONT capability profile when running the ont add command to add an ONU offline or running the ont confirm command to confirm an automatically discovered ONU.
Currently, the system provides seven default ONT capability profiles that are solidified in the system. The default profiles cannot be modified. The default profile IDs range from 1-7. The reserved ONT capability profile IDs are 8-16.
The contents of the capability profile restrict the port number that is used in commands for GEM port mapping, T-CONT/PQ mapping, and the ONT VLAN management.
The ONT capability profile must be configured according to the actual capability of the ONU. Different the capability profile parameters vary according to different ONUs.
Procedure
Step 1 Run the ont-profile add command to configure an ONT HG8546M capability profile.
- When you add an ONT capability profile, if the profile ID is not specified, the system automatically allocates the least idle profile ID; if the profile name is not specified, the system adopts the default name ont-profile_x, where, x is the corresponding ONT capability profile ID.
- The system supports up to 128 ONT capability profiles.
- The system default profiles include the MDU profile and several common ONT (such as OT925, HG850, and HG810) profiles, which can be directly used. It is recommended to manually configure an ONT capability profile only when the default ONT capability profile fails to meet actual requirements.
- When you add an MDU profile manually, the number of the ports must be set to zero.
Step 2 Run the display ont-profile command to query the ONT capability profile.
Tuesday, June 27, 2017
Some FAQs about Huawei S2700 S3700 S5700 S6700 Switch
Many engineer always confused Huawei switch when configuration and management, below are FAQs about Huawei S2700 S3700 S5700 S6700 Switch,
What Are the Functions of PIM Silent on a PIM Interface?
On the access layer, if the interface directly connected to a host is enabled with the PIM
protocol, PIM neighbors can be established on this interface to process various PIM protocol
packets. Such configuration, however, may bring security problems. For example, when
malicious hosts send a large number of pseudo PIM Hello packets, it may lead to the collapse
of the device.
To avoid the preceding problem, you can run the pim silent command on the interface to set
the interface to work in PIM silent state. After the interface enters the PIM silent state, it is
forbidden to receive or forward any PIM protocol packet. All PIM neighbors and the PIM
state machine on this interface are deleted and the interface automatically becomes a DR.
Meanwhile, the PIM silent function does not affect the IGMP function on the interface.
The PIM silent function is applicable only to the interface that is directly connected to the
network segment of user hosts, and only one PIM device can be connected to this network
segment.
When a Host Leaves a Group, How Does an IGMP Querier Judge Whether Any Other Members of the Group Exist on the Network Segment?
In IGMPv1, when a host leaves a multicast group, the host does not send any message. A
device considers that all multicast members have left a group when the timer of the group
expires.
In IGMPv2 and IGMPv3, a host sends a Leave message when leaving a group. After
receiving the Leave message, the querier sends a group-specific or source/group-specific
Query message to the network segment of the host. The destination address of the Query
message is the address of the multicast group and the group address in the message is also
filled in with the address of the multicast group.
If other members of the group exist on the network segment, they respond with Report
messages.
If no response is received when the timeout period ends, the querier considers that no
member of the group exists on the network segment and cancels forwarding multicast
data to the group.
Can the Hosts and Devices on the Same User Network Segment Run Different Versions of IGMP?
IGMP has three versions, namely IGMPv1, IGMPv2, and IGMPv3. Different IGMP versions
run on devices and hosts are compatible, but all the devices on the same network segment
must run IGMP of the same version. If the versions of IGMP run on the devices on the same
network segment are different, IGMP member relationships are chaotic.
Run the display igmp interface interface-type interface-number command on all the devices
on the same network segment to check the versions of IGMP run on the devices. If the
versions are not the same, modify the configuration.
Other questions about Huawei switch will be posted continually.
What Are the Functions of PIM Silent on a PIM Interface?
On the access layer, if the interface directly connected to a host is enabled with the PIM
protocol, PIM neighbors can be established on this interface to process various PIM protocol
packets. Such configuration, however, may bring security problems. For example, when
malicious hosts send a large number of pseudo PIM Hello packets, it may lead to the collapse
of the device.
To avoid the preceding problem, you can run the pim silent command on the interface to set
the interface to work in PIM silent state. After the interface enters the PIM silent state, it is
forbidden to receive or forward any PIM protocol packet. All PIM neighbors and the PIM
state machine on this interface are deleted and the interface automatically becomes a DR.
Meanwhile, the PIM silent function does not affect the IGMP function on the interface.
The PIM silent function is applicable only to the interface that is directly connected to the
network segment of user hosts, and only one PIM device can be connected to this network
segment.
When a Host Leaves a Group, How Does an IGMP Querier Judge Whether Any Other Members of the Group Exist on the Network Segment?
In IGMPv1, when a host leaves a multicast group, the host does not send any message. A
device considers that all multicast members have left a group when the timer of the group
expires.
In IGMPv2 and IGMPv3, a host sends a Leave message when leaving a group. After
receiving the Leave message, the querier sends a group-specific or source/group-specific
Query message to the network segment of the host. The destination address of the Query
message is the address of the multicast group and the group address in the message is also
filled in with the address of the multicast group.
If other members of the group exist on the network segment, they respond with Report
messages.
If no response is received when the timeout period ends, the querier considers that no
member of the group exists on the network segment and cancels forwarding multicast
data to the group.
Can the Hosts and Devices on the Same User Network Segment Run Different Versions of IGMP?
IGMP has three versions, namely IGMPv1, IGMPv2, and IGMPv3. Different IGMP versions
run on devices and hosts are compatible, but all the devices on the same network segment
must run IGMP of the same version. If the versions of IGMP run on the devices on the same
network segment are different, IGMP member relationships are chaotic.
Run the display igmp interface interface-type interface-number command on all the devices
on the same network segment to check the versions of IGMP run on the devices. If the
versions are not the same, modify the configuration.
Other questions about Huawei switch will be posted continually.
Monday, June 26, 2017
Introduction for TE Tunnel Protection Group on Huawei Access Network Equipment
Introduction for TE Tunnel Protection Group on Huawei Access Network Equipment.
A tunnel protection group protects end-to-end MPLS TE tunnels. If a working tunnel in a protection group fails, traffic switches to a protection tunnel, minimizing traffic interruptions.
Related Concepts
As shown in the Figure, concepts related to a tunnel protection group are as follows:
Working tunnel: a tunnel to be protected.
Protection tunnel: a tunnel that protects a working tunnel.
Protection switchover: switches traffic from a faulty working tunnel to a protection tunnel in a tunnel protection group, which improves network reliability.
A tunnel protection group protects end-to-end MPLS TE tunnels. If a working tunnel in a protection group fails, traffic switches to a protection tunnel, minimizing traffic interruptions.
Related Concepts
As shown in the Figure, concepts related to a tunnel protection group are as follows:
Working tunnel: a tunnel to be protected.
Protection tunnel: a tunnel that protects a working tunnel.
Protection switchover: switches traffic from a faulty working tunnel to a protection tunnel in a tunnel protection group, which improves network reliability.
Primary tunnels tunnel-1 and tunnel-2, and the bypass tunnel tunnel-3 are established on the ingress Access Node
Tunnel-3 is specified as a protection tunnel for primary tunnels tunnel-1 and tunnel-2 on Access Node. If the configured fault detection mechanism on the ingress detects a fault in tunnel-1, traffic switches to tunnel-3. Access Node attempts to reestablish tunnel-1. If tunnel-1 is successfully established, traffic switches back to the primary tunnel.
Implementation
A TE tunnel protection group uses a configured protection tunnel to protect traffic on the working tunnel to improve tunnel reliability. To ensure the improved performance of the protection tunnel, the protection tunnel must exclude links and nodes through which the working tunnel passes during network planning.
Protection mode
A tunnel protection group works in either 1:1 or N:1 mode. The 1:1 mode enables a protection tunnel to protect only a single working tunnel. The N:1 mode enables a protection tunnel to protect more than one working tunnel.
More related:
MA5600V800R00X series devices load the IO data package
P2P Access: Configuring FTTH Service
Sunday, June 25, 2017
Is Optical Amplifier board TN12OAU101 an indispensable element on Huawei DWDM Equipment?
TN12OAU101 is a WDM optical amplifier board, to amplifies C band optical signals at Gain Range 20dB to 31dB. TN12OAU101 part number is 03030LMK, some other version like TN11OAU1 and TN13OAU1 with different system compatibility and feature supported. TN12OAU1 have feature code like 03 and 05, different Gain Range.
- Amplifies the input optical signals in C band.
- Applied to Huawei OSN8800, OSN6800,OSN3800
- Supports the system to transmit services over different fiber spans without electrical regeneration.
- Gain adjustment of OAU101: 20dB to 31dB.
- Provides an in-service monitoring port (MON).
- Supports the gain locking and power locking modes.
- The EDFA inside board has transient control function.
- Detects and reports the optical power.
- Monitors the temperature of the pump laser.
- Detects current of pump driving, back facet and pump cooling; temperature of pump laser and ambient temperature of board.
- Supports Optical-layer ASON.
Thursday, June 22, 2017
OT928G loopback cannot be configured due to U2000 internal problem
Issue Description
It is required to configure loopback on OT928G through
U2000 management system but when it is done system
pop ups an alarm informing that operation failed.
MA5680T MA5600V800R008C01
U2000 V100R002C01SPC004
pop ups an alarm informing that operation failed.
MA5680T MA5600V800R008C01
U2000 V100R002C01SPC004
Alarm Information
Set a Local Loopback operation failed
Failure cause: The version does not match
Failure cause: The version does not match
Handling Process
Process to configure
loopback through U2000 was verified and tested to confirm it is correct and it
was but the failure was gottenVersions compatibility was verified and it was confirmed U2000 supported Huawei MA5600T base version
Process was recurred to collect some info and logs that were sent to R&D who finally confirmed it was U2000 problem so, they provided a temporal solution replacing file GPON_operdesc.xml on following path.
U2000/server/nemgr/nemgr_access/dcp/mib/gpon/GPON_operdesc.xml
However, this problem has been already solved on patch SPC501 for U2000
However, this problem has been already solved on patch SPC501 for U2000
Root Cause
Procedure to configure loopback is not correct
U2000 and OLT versions are not compatible
Software system problem
U2000 and OLT versions are not compatible
Software system problem
Suggestions
Null
Wednesday, June 21, 2017
What Is MAC Address Management?
MAC address management is a basic Layer 2 management feature that enables system administrators to use the functions listed in the following table.
Sub-function of MAC Address Management:
Setting the MAC address aging time
Limiting the number of learnable dynamic MAC addresses
Setting the static MAC address
Benefits
Benefits for Carriers
1, The system ages dynamic MAC addresses to ensure timely updates of the MAC address table. If the MAC address table is full and not updated, the system will fail to learn new MAC addresses and will consequently fail to forward data.
2, By limiting the number of learnable dynamic MAC addresses, the system administrator can limit the number of MAC addresses that can be used to enter the network and hence alleviate the load of network devices.
3, By configuring static MAC addresses, the system administrator prohibits unauthorized users from accessing the system.
Benefits for Subscribers
Improved user security: After the system administrator sets the static MAC address of a service port and sets the maximum number of learnable MAC addresses to 0, the port receives only user data carrying the specified static MAC address.
The access node provides multiple MAC address security features to protect networks against forged MAC addresses, please refer to 23 MAC Address Security Features.
Address Management Process
MAC address management includes MAC address table establishment and management.
Establishing MAC Address Tables
The system establishes a MAC address table by learning source MAC addresses or after users configure static MAC address entries.
MAC address learning
− When Huawei OLT functions as a Layer 2 switching device, it learns MAC addresses in the distributed mode. Specifically, each board learns the source MAC address of packets sent from the board of its own and then forwards packets according to their destination MAC addresses. The learned MAC addresses are stored in the system buffer. Generally, the system buffer can hold a limited number of MAC address entries. If all these entries are filled in, no more MAC addresses can be learned.
− Configuration command: mac-address learning vlan
Configuration of static MAC address entries
− A user can manually configure static MAC address entries in which user device MAC addresses are bound to ports. After this configuration, the packets whose MAC addresses are included in the MAC address entries are always forwarded through the bound ports. This configuration improves the efficiency for forwarding packets and improves the security of ports because it denies access from unauthenticated users. This method of establishing MAC address tables is widely used in private networks.
− Configuration command: mac-address static
The following table shows an example of a simplified MAC address table established by configuring static MAC address entries. The table lists the mapping between MAC addresses, ports, and VLAN IDs.
Managing MAC Address Tables
When managing MAC address tables, users can configure MAC-related attributes as allowed by system resources and network security policies against potential risks. The optimized MAC address tables can better meet requirements of a live network. These MAC-related attributes are as follows:
Maximum number of MAC addresses learned based on service flows
− After the number of access users reaches the limit, no new access user addresses will be learned. This attribute setting applies to networks, such as residential access networks and low-security internal enterprise networks, that have fixed access users but are not sufficiently secure.
Setting the function of sensing excess MAC addresses
When a lot of MAC addresses are learnt by the system, it is difficult for trouble locating. When the function of sensing excess MAC addresses is enabled, the board software queries the actual MAC address specifications of the board every 15 minutes and determines whether an alarm needs to be reported according to the query result. If the query result exceeds the upper threshold for sensing excess MAC addresses set by users, an excess MAC address alarm is generated. If the query result is smaller than the lower threshold for sensing excess MAC addresses set by users, a fault clearing alarm is generated.
Configuration command: overload-aware mac-address
MAC address aging
Generally, the system automatically establishes a MAC address table by learning source MAC addresses. The established MAC address table has to be updated according to network changes. However, after the network topology changes, the dynamic MAC address entries will not be automatically updated in a timely manner. Then the system cannot learn more MAC addresses and user data
Sub-function of MAC Address Management:
Setting the MAC address aging time
Limiting the number of learnable dynamic MAC addresses
Setting the static MAC address
Benefits
Benefits for Carriers
1, The system ages dynamic MAC addresses to ensure timely updates of the MAC address table. If the MAC address table is full and not updated, the system will fail to learn new MAC addresses and will consequently fail to forward data.
2, By limiting the number of learnable dynamic MAC addresses, the system administrator can limit the number of MAC addresses that can be used to enter the network and hence alleviate the load of network devices.
3, By configuring static MAC addresses, the system administrator prohibits unauthorized users from accessing the system.
Benefits for Subscribers
Improved user security: After the system administrator sets the static MAC address of a service port and sets the maximum number of learnable MAC addresses to 0, the port receives only user data carrying the specified static MAC address.
The access node provides multiple MAC address security features to protect networks against forged MAC addresses, please refer to 23 MAC Address Security Features.
Address Management Process
MAC address management includes MAC address table establishment and management.
Establishing MAC Address Tables
The system establishes a MAC address table by learning source MAC addresses or after users configure static MAC address entries.
MAC address learning
− When Huawei OLT functions as a Layer 2 switching device, it learns MAC addresses in the distributed mode. Specifically, each board learns the source MAC address of packets sent from the board of its own and then forwards packets according to their destination MAC addresses. The learned MAC addresses are stored in the system buffer. Generally, the system buffer can hold a limited number of MAC address entries. If all these entries are filled in, no more MAC addresses can be learned.
− Configuration command: mac-address learning vlan
Configuration of static MAC address entries
− A user can manually configure static MAC address entries in which user device MAC addresses are bound to ports. After this configuration, the packets whose MAC addresses are included in the MAC address entries are always forwarded through the bound ports. This configuration improves the efficiency for forwarding packets and improves the security of ports because it denies access from unauthenticated users. This method of establishing MAC address tables is widely used in private networks.
− Configuration command: mac-address static
The following table shows an example of a simplified MAC address table established by configuring static MAC address entries. The table lists the mapping between MAC addresses, ports, and VLAN IDs.
Managing MAC Address Tables
When managing MAC address tables, users can configure MAC-related attributes as allowed by system resources and network security policies against potential risks. The optimized MAC address tables can better meet requirements of a live network. These MAC-related attributes are as follows:
Maximum number of MAC addresses learned based on service flows
− After the number of access users reaches the limit, no new access user addresses will be learned. This attribute setting applies to networks, such as residential access networks and low-security internal enterprise networks, that have fixed access users but are not sufficiently secure.
Setting the function of sensing excess MAC addresses
When a lot of MAC addresses are learnt by the system, it is difficult for trouble locating. When the function of sensing excess MAC addresses is enabled, the board software queries the actual MAC address specifications of the board every 15 minutes and determines whether an alarm needs to be reported according to the query result. If the query result exceeds the upper threshold for sensing excess MAC addresses set by users, an excess MAC address alarm is generated. If the query result is smaller than the lower threshold for sensing excess MAC addresses set by users, a fault clearing alarm is generated.
Configuration command: overload-aware mac-address
MAC address aging
Generally, the system automatically establishes a MAC address table by learning source MAC addresses. The established MAC address table has to be updated according to network changes. However, after the network topology changes, the dynamic MAC address entries will not be automatically updated in a timely manner. Then the system cannot learn more MAC addresses and user data
Tuesday, June 20, 2017
I Want to Reset Huawei OLT MA5600T Password, Then How Should I Do?
My Huawei OLT MA5600T Password is known by others, so I need to reset the password, then how should I do?
After using the device, the user may change the default user name and password. If you forget the password of user root, please perform the following methods. Method 2 is recommended.
Method 1: Load the empty database matched the device again through DoS. After restarting the device, log in to the system by using the default root password admin (OLT) or mduadmin (MDU). This method will lead to loss of data configurations and the user needs to configure the data again.
Method 2: Modify the configuration file using the U2000.
1. On the U2000, choose Administration > NE Security Management > LCT User Management from the main menu.
2. On the LCT User Management tab page, select NE User and then Device Type. Select the desired device name from the Device Name column and user name from the Name column. In the displayed dialog box, choose Set Password to set the new password.
After using the device, the user may change the default user name and password. If you forget the password of user root, please perform the following methods. Method 2 is recommended.
Method 1: Load the empty database matched the device again through DoS. After restarting the device, log in to the system by using the default root password admin (OLT) or mduadmin (MDU). This method will lead to loss of data configurations and the user needs to configure the data again.
Method 2: Modify the configuration file using the U2000.
1. On the U2000, choose Administration > NE Security Management > LCT User Management from the main menu.
2. On the LCT User Management tab page, select NE User and then Device Type. Select the desired device name from the Device Name column and user name from the Name column. In the displayed dialog box, choose Set Password to set the new password.
This method does not require a device restart or services are not interrupted.
Method 3: If the device is managed by the NMS, modify the configuration file on the NMS as follows:
1. Back up the configuration file of the device on the NMS.
2. Open the configuration file and find out the record of changing the root password, as shown in boldface in the following display.
3.[MA5600V800R0013: 6888]
4.#
5.[global-config]
6.
7. <global-config>
8.
9. terminal user name buildrun_new lww231 *[)!AAYS*Y&aU86K;V-a@AUA!!* 1 2015:06:0410.11.:17:07:25 2015:06:04:17:07:25 root 2 6 -----
12.
13. terminal user name buildrun_new bmsmpls *[4P]`OUIa%=[G]0U3=OWJY1!!* 0 2015:06:
14.
15.08:15:01:02 2015:06:08:15:01:02 root 3 65535 -----
16.
17.adsl mode switch-to ADSL
18.19.vdsl mode switch-to normal20.Delete the boldface part and then save the configuration file.
21.Load the modified configuration file to the system through the NMS and activate the configuration file.
22.Log in to the device by using the default root password admin (OLT) or mduadmin (MDU)
Monday, June 19, 2017
Logical fiber still green even if real fiber is cut and we have R_LOS alarm
Issue Description
Customer M complains the following problem:
we have real fiber cut and R_LOS alarm is reported, but the logical fiber color on U2000 topology is still green even if the relevant port reports R_LOS. This makes customers maintenance difficult to report fiber cut on time and they pushed Huawei CS to solve the problem ASAP.
Please check the pictures attached in "problem scene" file to see the problem.
we have real fiber cut and R_LOS alarm is reported, but the logical fiber color on U2000 topology is still green even if the relevant port reports R_LOS. This makes customers maintenance difficult to report fiber cut on time and they pushed Huawei CS to solve the problem ASAP.
Please check the pictures attached in "problem scene" file to see the problem.
Alarm Information
R_LOS on port but relevant fiber does not become red.
Handling Process
To solve this problem you can do as following:
1) Stop fault process in sysmonitor.
2) Use "root" user to login your running service server.
3) Put the files in the attachment of this case (input.sql and IPServiceNum.sh) in server path /tmp
Note: use bin format to load these files to server.
4)modify this file right by this command:
cd /tmp
chmod +775 IPServiceNum.sh
5)do this file script by this command:
sh IPServiceNum.sh
6) after that, the system will ask you to input some information : please input like following OSS_ROOT:/opt/U2000
database server name: DBSVR
database user : sa
database password: by default it is null, but if you have changed it you need to enter current password
7) start fault process in sysmonitor.
8) Clear R_LOS alarm manually in NMS, after you clear this alarm, and if this fiber still cut, the R_LOS for this fiber will be reported to NMS again, then this fiber will be turned to red in NMS.
1) Stop fault process in sysmonitor.
2) Use "root" user to login your running service server.
3) Put the files in the attachment of this case (input.sql and IPServiceNum.sh) in server path /tmp
Note: use bin format to load these files to server.
4)modify this file right by this command:
cd /tmp
chmod +775 IPServiceNum.sh
5)do this file script by this command:
sh IPServiceNum.sh
6) after that, the system will ask you to input some information : please input like following OSS_ROOT:/opt/U2000
database server name: DBSVR
database user : sa
database password: by default it is null, but if you have changed it you need to enter current password
7) start fault process in sysmonitor.
8) Clear R_LOS alarm manually in NMS, after you clear this alarm, and if this fiber still cut, the R_LOS for this fiber will be reported to NMS again, then this fiber will be turned to red in NMS.
Root Cause
After analyzing this problem we found that the root cause
of the problem is the following:
During installing instance, the information for file ipe2emgr_alarm_define_ext.xml can not put the alarm information into the table tbl_cur_alm which made the fiber remains still green even if we have R_LOS alarm in the corresponding port.
During installing instance, the information for file ipe2emgr_alarm_define_ext.xml can not put the alarm information into the table tbl_cur_alm which made the fiber remains still green even if we have R_LOS alarm in the corresponding port.
Suggestions
If you have the same case in your site, please to check
with R&D before performing the procedure described in this case. If they
confirm the solution according to your site specifications then you can try it.
More related
MA5600T Series Equipment Downgrade Guidebook
GPON Board common command guide
How to configure the Management Channel Between OLT and ONU?
Sunday, June 18, 2017
What's the difference between Huawei GPON board GPSF and GPHF?
Thursday, June 15, 2017
Do you know Huawei S5320-EI Series Switches?
Huawei S5320-EI series enhanced gigabit Ethernet switches (S5320-EI for short) are next-generation energysaving switches developed by Huawei to meet the demand for high-bandwidth access and Ethernet multiservice aggregation. Based on the cutting-edge hardware and Huawei Versatile Routing Platform (VRP) software, Huawie S5320-EI provides a large switching capacity and high-density GE ports to implement 10 Gbit/s upstream transmissions. The S5320-EI is for use in various network scenarios. For example, it can function as an edge device on the MAN, an access or aggregation switch on a campus network, a gigabit access switch in an Internet data center (IDC), or a desktop switch to provide 1000 Mbit/s access for terminals. The S5320- EI is easy to install and maintain, reducing workloads for network planning, construction, and maintenance. The S5320-EI uses advanced reliability, security, and energy conservation technologies, helping enterprise
customers build a next generation IT network.
Comprehensive reliability mechanism
• Besides STP, RSTP, and MSTP, the S5320-EI like S5320-50X-EI-46S-AC supports enhanced Ethernet reliability technologies such as Smart Link and RRPP (Rapid Ring Protection Protocol), which implement millisecond-level protection switchover and ensure network reliability. It also provides Smart Link multi-instance and RRPP multiinstance to implement load balancing among links, optimizing bandwidth usage.
• The S5320-EI supports enhanced trunk (E-Trunk) that enables a CE to be dual-homed to two PEs (S5320s).
E-Trunk greatly enhances link reliability between devices and implements link aggregation between
devices. This improves reliability of access devices.
• The S5320-EI supports the Smart Ethernet Protection (SEP) protocol, a ring network protocol applied to the link layer on an Ethernet network. SEP can be used on open ring networks and can be deployed on upper-layer aggregation devices to provide fast switchover (within 50 ms), ensuring non-stop transmission of services. SEP features simplicity, high reliability, fast switchover, easy maintenance, and flexible topology, facilitating network planning and management.
• The S5320-EI supports Ethernet Ring Protection Switching (ERPS), also referred to as G.8032. As the latest ring network protocol, ERPS was developed based on traditional Ethernet MAC and bridging functions and uses mature Ethernet OAM function and a Ring Automatic Protection Switching(R-APS) mechanism to implement millisecond-level protection switching. ERPS supports various services and allows flexible networking, helping customers build a network with lower OPEX and CAPEX.
• The S5320-EI supports redundant power supplies, and can use an AC power supply and a DC power simultaneously. Users can choose a single power supply or use two power supplies to ensure device reliability.
• The S5320-EI supports VRRP, and can set up VRRP groups with other Layer 3 switches. VRRP provides redundant routes to ensure stable and reliable communication. Multiple equal-cost routes to an uplink device can be configured on the S5320-EI to provide route redundancy. When an active route is unreachable, traffic is switched to a backup route.
• The S5320-EI supports Bidirectional Forwarding Detection (BFD) and provides millisecond-level detection for protocols such as OSPF, IS-IS, VRRP, and PIM to improve network reliability. The S5320-EI complies with IEEE 802.3ah and 802.1ag. IEEE 802.3ah defines the mechanism for detecting faults on direct links over the Ethernet in the first mile, and 802.1ag defines the mechanism for end-to-end service fault detection. The S5320-EI supports Y.1731. Besides fast end-to-end service fault detection, the S5320-EI can use the performance measurement tools defined in Y.1731 to monitor network performance, providing accurate data about network quality.
More related:
customers build a next generation IT network.
Comprehensive reliability mechanism
• Besides STP, RSTP, and MSTP, the S5320-EI like S5320-50X-EI-46S-AC supports enhanced Ethernet reliability technologies such as Smart Link and RRPP (Rapid Ring Protection Protocol), which implement millisecond-level protection switchover and ensure network reliability. It also provides Smart Link multi-instance and RRPP multiinstance to implement load balancing among links, optimizing bandwidth usage.
• The S5320-EI supports enhanced trunk (E-Trunk) that enables a CE to be dual-homed to two PEs (S5320s).
E-Trunk greatly enhances link reliability between devices and implements link aggregation between
devices. This improves reliability of access devices.
• The S5320-EI supports the Smart Ethernet Protection (SEP) protocol, a ring network protocol applied to the link layer on an Ethernet network. SEP can be used on open ring networks and can be deployed on upper-layer aggregation devices to provide fast switchover (within 50 ms), ensuring non-stop transmission of services. SEP features simplicity, high reliability, fast switchover, easy maintenance, and flexible topology, facilitating network planning and management.
• The S5320-EI supports Ethernet Ring Protection Switching (ERPS), also referred to as G.8032. As the latest ring network protocol, ERPS was developed based on traditional Ethernet MAC and bridging functions and uses mature Ethernet OAM function and a Ring Automatic Protection Switching(R-APS) mechanism to implement millisecond-level protection switching. ERPS supports various services and allows flexible networking, helping customers build a network with lower OPEX and CAPEX.
• The S5320-EI supports redundant power supplies, and can use an AC power supply and a DC power simultaneously. Users can choose a single power supply or use two power supplies to ensure device reliability.
• The S5320-EI supports VRRP, and can set up VRRP groups with other Layer 3 switches. VRRP provides redundant routes to ensure stable and reliable communication. Multiple equal-cost routes to an uplink device can be configured on the S5320-EI to provide route redundancy. When an active route is unreachable, traffic is switched to a backup route.
• The S5320-EI supports Bidirectional Forwarding Detection (BFD) and provides millisecond-level detection for protocols such as OSPF, IS-IS, VRRP, and PIM to improve network reliability. The S5320-EI complies with IEEE 802.3ah and 802.1ag. IEEE 802.3ah defines the mechanism for detecting faults on direct links over the Ethernet in the first mile, and 802.1ag defines the mechanism for end-to-end service fault detection. The S5320-EI supports Y.1731. Besides fast end-to-end service fault detection, the S5320-EI can use the performance measurement tools defined in Y.1731 to monitor network performance, providing accurate data about network quality.
More related:
Different VLAN with the same IP address segment communicate through the layer three switches
Wednesday, June 14, 2017
ARP on main control board SCUN, SCUH, MPLA is am important element when engineer choose OLT
ARP on main control board SCUN and SCUH on Huawei MA5600T, MPLA on MA5800 is am important element when engineer choose OLT, then what is ARP?
The Address Resolution Protocol (ARP) is an Internet protocol used to map IP addresses to MAC addresses.
Purpose
To communicate with each other, the sending device must know the network-layer IP address of the receiving device. IP datagrams, however, must be encapsulated with MAC addresses before they can be transmitted over the physical network. Therefore, a resolution from the known IP address to a MAC address is required.
ARP was developed to enable communication between devices.
Dynamic ARP: Devices dynamically learn and update the mapping between IP addresses and MAC addresses by exchanging ARP messages. Real-time communication is a priority, or network resources are insufficient.
Static ARP: The mapping between IP addresses and MAC addresses is manually created and cannot be dynamically modified. Communication security is a priority, and network resources are sufficient.
Gratuitous ARP:A device broadcasts gratuitous ARP packets that carry the local IP address as both the source and destination IP addresses to notify the other devices on the same network segment of its address information. Gratuitous ARP is used to check whether the local IP address conflicts with that of another device, to notify other devices on the same network segment of the new MAC address after the local network interface card is replaced, or to notify master/slave switchovers in a Virtual Router Redundancy Protocol (VRRP) backup group.
Benefits
ARP ensures Ethernet communication by mapping IP addresses at the network layer to MAC addresses at the link layer on Ethernet networks.
Principles
ARP involves the following concepts:
Address Resolution Protocol (ARP) messages
An ARP message can be an ARP request or reply message. Figure below shows the ARP message format.
− Static ARP entries are manually configured and maintained by a network administrator. Static ARP entries can neither be aged nor be overwritten by dynamic ARP entries.
Before sending IP datagrams, a host searches the ARP table for the MAC address corresponding to the destination IP address.
− If the ARP table contains the corresponding MAC address, the host directly sends the IP datagrams to the MAC address instead of sending an ARP Request message.
− If the ARP table does not contain the corresponding MAC address, the host broadcasts an ARP Request message to request the MAC address of the destination host.
Reverse Address Resolution Protocol (RARP)
If only the MAC address of a host is available, the host can send and receive RARP messages to obtain its IP address.
To do so, the network administrator must establish the mapping between MAC addresses and IP addresses on a gateway. When a new host must be configured, its RARP client requests the host's IP address from the RARP server on the gateway.
The Address Resolution Protocol (ARP) is an Internet protocol used to map IP addresses to MAC addresses.
Purpose
To communicate with each other, the sending device must know the network-layer IP address of the receiving device. IP datagrams, however, must be encapsulated with MAC addresses before they can be transmitted over the physical network. Therefore, a resolution from the known IP address to a MAC address is required.
ARP was developed to enable communication between devices.
Dynamic ARP: Devices dynamically learn and update the mapping between IP addresses and MAC addresses by exchanging ARP messages. Real-time communication is a priority, or network resources are insufficient.
Static ARP: The mapping between IP addresses and MAC addresses is manually created and cannot be dynamically modified. Communication security is a priority, and network resources are sufficient.
Gratuitous ARP:A device broadcasts gratuitous ARP packets that carry the local IP address as both the source and destination IP addresses to notify the other devices on the same network segment of its address information. Gratuitous ARP is used to check whether the local IP address conflicts with that of another device, to notify other devices on the same network segment of the new MAC address after the local network interface card is replaced, or to notify master/slave switchovers in a Virtual Router Redundancy Protocol (VRRP) backup group.
Benefits
ARP ensures Ethernet communication by mapping IP addresses at the network layer to MAC addresses at the link layer on Ethernet networks.
Principles
ARP involves the following concepts:
Address Resolution Protocol (ARP) messages
An ARP message can be an ARP request or reply message. Figure below shows the ARP message format.
ARP table
An ARP table, for example SCUN on Huawei MA5603T ARP table is 8192, contains the latest mapping between IP addresses and MAC addresses. If a host always broadcasts an ARP Request message for a MAC address before it sends an IP datagram, network communication traffic will greatly increase. Furthermore, all other hosts on the network have to receive and process the ARP Request messages, which lowers network efficiency. To solve this problem, an ARP table is maintained on each host to ensure efficient ARP operations. The mapping between an IP address and a MAC address is called an ARP entry.
ARP entries can be classified as dynamic or static.
− Dynamic ARP entries are automatically generated and maintained by using ARP messages. Dynamic ARP entries can be aged and overwritten by static ARP entries.− Static ARP entries are manually configured and maintained by a network administrator. Static ARP entries can neither be aged nor be overwritten by dynamic ARP entries.
Before sending IP datagrams, a host searches the ARP table for the MAC address corresponding to the destination IP address.
− If the ARP table contains the corresponding MAC address, the host directly sends the IP datagrams to the MAC address instead of sending an ARP Request message.
− If the ARP table does not contain the corresponding MAC address, the host broadcasts an ARP Request message to request the MAC address of the destination host.
Reverse Address Resolution Protocol (RARP)
If only the MAC address of a host is available, the host can send and receive RARP messages to obtain its IP address.
To do so, the network administrator must establish the mapping between MAC addresses and IP addresses on a gateway. When a new host must be configured, its RARP client requests the host's IP address from the RARP server on the gateway.
Capabilities of Supporting Clocks on Huawei OSN2500
The clocks supported by the equipment and the clock protection are defined.
Basic Functions
Huawei OptiX OSN 2500 have the following functions:
Tracing of the external clock source, line clock source, tributary clock source and internal
clock source.
Non-SSM, standard SSM and extended SSM.
Clock working modes compliant with ITU-T G.781, such as locked, hold-over, and free
run.
Output of the line clock, tributary clock and external clock.
Tributary re-timing.
ASON clock tracing scheme.
Clock Protection
Huawei OptiX OSN 2500 can realize the clock protection switching in the following ways:
l Do not enable the SSM, and then perform the clock source selection and switching
according to the priority list. In this case, do not configure two clocks in two directions on
one NE into the priority list. Otherwise, the clocks form a loop.
l Enable the standard SSM mode, and then configure the priority list to ensure that the OptiX
OSN 2500 can automatically select the clock source with the highest priority to avoid the
locked loop.
l Enable the extended SSM mode. Use the fifth to eighth bits of the S1 byte to define the
quality of the clock source, and use the first to fourth bits of the S1 byte to define the clock
source ID. Thus, the clock loop can be avoided. The principles for setting the clock IDs are
as follows:
– All external BITSs should be assigned with clock IDs.
– In the case of nodes with external BITSs, the internal clocks of these nodes should be
assigned with clock IDs.
– In the case of nodes that access the chain or ring network to another ring network, the
clock sources of these nodes should be assigned with clock IDs.
– In the case of nodes that access the chain or ring network to another ring network, when
the clock tracing level includes the line clock source, the line clock sources accessed to
another ring network should be assigned with clock IDs.
Basic Functions
Huawei OptiX OSN 2500 have the following functions:
Tracing of the external clock source, line clock source, tributary clock source and internal
clock source.
Non-SSM, standard SSM and extended SSM.
Clock working modes compliant with ITU-T G.781, such as locked, hold-over, and free
run.
Output of the line clock, tributary clock and external clock.
Tributary re-timing.
ASON clock tracing scheme.
Clock Protection
Huawei OptiX OSN 2500 can realize the clock protection switching in the following ways:
l Do not enable the SSM, and then perform the clock source selection and switching
according to the priority list. In this case, do not configure two clocks in two directions on
one NE into the priority list. Otherwise, the clocks form a loop.
l Enable the standard SSM mode, and then configure the priority list to ensure that the OptiX
OSN 2500 can automatically select the clock source with the highest priority to avoid the
locked loop.
l Enable the extended SSM mode. Use the fifth to eighth bits of the S1 byte to define the
quality of the clock source, and use the first to fourth bits of the S1 byte to define the clock
source ID. Thus, the clock loop can be avoided. The principles for setting the clock IDs are
as follows:
– All external BITSs should be assigned with clock IDs.
– In the case of nodes with external BITSs, the internal clocks of these nodes should be
assigned with clock IDs.
– In the case of nodes that access the chain or ring network to another ring network, the
clock sources of these nodes should be assigned with clock IDs.
– In the case of nodes that access the chain or ring network to another ring network, when
the clock tracing level includes the line clock source, the line clock sources accessed to
another ring network should be assigned with clock IDs.
Monday, June 12, 2017
How to Configuring the P2P Optical Fiber Access Service?
Point-to-point (P2P) optical access means the point-to-point FTTx access based on the combination between their P2P optical access board and the ONUs. So as to satisfy the users' requirements for the next generation access equipment which integrates video Voice, and data services.
Configuring the FTTH P2P Optical Fiber Access Service
Users connected to the OLT through an ONT, and are are provided with the Internet, VoIP, and IPTV service through a same port.
Service Requirements
Configuring the FTTH P2P Optical Fiber Access Service
Users connected to the OLT through an ONT, and are are provided with the Internet, VoIP, and IPTV service through a same port.
Service Requirements
- ONT_1 and ONT_2 are provided with the triple play service through FTTH .
- The Internet access service is provided in the PPPoE access mode.
- The IPTV users connected to ONT_1 can watch all the programs, and the IPTV user connected to ONT_2 can watch only program BTV-1.
- The VoIP service and the IPTV service are provided in the DHCP mode and obtain IP addresses from the DHCP server in the DHCP option-60 mode.
- After receiving different traffic streams, the OLT provides different QoS guarantees to the traffic layers according to the priorities of the traffic streams.
- Traffic streams are differentiated on the OLT by the user-side VLAN (C-VLAN).
Prerequisite
- The OLT is connected to the upper-layer devices such as the BRAS, multicast server, SoftX3000, and DHCP server.
- The VLAN of the LAN switch port connected to the OLT is the same as the upstream VLAN of the OLT.
1, Configure the Internet access service on the OLT.
2, Configure the VoIP service on the OLT.
3, Configure the IPTV service on the OLT.
Result
After the related upstream device and downstream device are configured, the triple play service (Internet, VoIP, and IPTV services) is available.
The Internet user can access the Internet in the PPPoE mode.
The VoIP user can make and receive phone calls.
The IPTV user connected to port 0/5/2 can watch all the programs, and the IPTV user connected to port 0/5/3 can watch only program BTV-1.
Configuring MDUs Cascaded to an OLT
MDUs are cascaded to an Huawei MA5800 through the P2P board, derived savings upstream optical fibers and simplifying the network and service configuration.
Service Requirements
MDU_1 and MDU_2 are connected to an OLT through GE cascading, implementing the Internet access service.
The Internet access service is provided in the PPPoE dialing mode.
Procedure
Configure the OLT.
Configure the MDUs.
The configurations of MDU_1 and MDU_2 are the same. The configuration of MDU_1 is used as an example.
A. Create a VLAN and add an upstream port to the VLAN.
SmartAX MA5800 Multi-service Access Module
Feature Guide 4 P2P Optical Access
Issue 02 (2017-01-20) Huawei Proprietary and Confidential
Create smart SVLAN 200. The upstream port is port 0/0/1.
The security of the ASU is to be the same as the CVLAN of Huawei OLT. Huawei (config) #vlan 200 smart huawei (config) #port vlan 200 0/0 1
B. Configure a service port.
According to the actual conditions, an MDU supports multiple access modes. In this example, the Ethernet port 0/3/1 is used. For other access modes, see the corresponding configuration guide of the MDU. Huawei (config) # service-port Vlan 200 eth 0/3/1 multi-service user-vlan untagged rx-cttr 6 tx-cttr 6
C. Save the data. Huawei (config) #save
Sunday, June 11, 2017
How to Turn on the Debug Switch in DC Server Process?
Issue Description
Q:
How to turn on the debug switch in the DC Server process?
How to turn on the debug switch in the DC Server process?
Alarm Information
Null
Handling Process
A:
There are two methods to turn on the debug switch in the DC Server process:
I. Find the DC_DEBUGINFO_SWITCH parameter in the $n2000\server\conf\dc.cfg file (under the n2000 installation directory):
#For debugging the data center
DC_DEBUGINFO_SWITCH = 1
1: indicates starting the system monitor; 0: indicates closing the system monitoring function
Modify the parameter to 1 to turn on the debug switch. After several operations resulting in the DCServer faults, two log files containing the DC field will be generated under $n2000/server/log.
DC_UA5000G_Alarm_Info.log0 and DC_172.20.17.70-161_Info.log0 (172.20.17.70 refers to the IP address of the operated device in the DCServer),
After collecting the debug information, you are recommended to turn off the switch timely to avoid generating further log files.
2. Operate as per the following steps:
telnet 10.71.61.45 9810
Firstly, telnet to the port 9810 of the NM server. 10.71.61.45 corresponds to the IP address of the NM server
iMAP>setdbg
ProcessID : 148 (The internal process number corresponding to the DCServer)
Scope(format is "module_submodule". default, all module) ://enter
Debug level as following:
0, None;
1, Error.
2, Error and Warning.
3, Error Warning and Info.
Please select level : 3
Debug output orient as following:
0, Standard output.
1, file.
2, share memory.
3, EmfExamDm.
Please select orient : 1
Setting succeeded!
After several operations resulting in the DC Server fault, stop the debug switch.
iMAP>setdbg
Process ID : 148
Scope(format is "module_submodule". default, all module) :
Debug level as following:
0, Null;
1, Error.
2, Error and Warning.
3, Error Warning and Info.
Please select level : 0
Debug output orient as following:
0, Standard output.
1, file.
2, share memory.
3, EmfExamDm.
Please select orient : 0
Setting succeeded!
Obtain the debug information about the DCServer process generated under $n2000/server/debug.
3. The information generated from the first method is less and easier for analysis, so the Method 1is normally used to identify general problems. The second method can generate more information, so it is more complicated for analysis, and often used to identify difficult problems.
There are two methods to turn on the debug switch in the DC Server process:
I. Find the DC_DEBUGINFO_SWITCH parameter in the $n2000\server\conf\dc.cfg file (under the n2000 installation directory):
#For debugging the data center
DC_DEBUGINFO_SWITCH = 1
1: indicates starting the system monitor; 0: indicates closing the system monitoring function
Modify the parameter to 1 to turn on the debug switch. After several operations resulting in the DCServer faults, two log files containing the DC field will be generated under $n2000/server/log.
DC_UA5000G_Alarm_Info.log0 and DC_172.20.17.70-161_Info.log0 (172.20.17.70 refers to the IP address of the operated device in the DCServer),
After collecting the debug information, you are recommended to turn off the switch timely to avoid generating further log files.
2. Operate as per the following steps:
telnet 10.71.61.45 9810
Firstly, telnet to the port 9810 of the NM server. 10.71.61.45 corresponds to the IP address of the NM server
iMAP>setdbg
ProcessID : 148 (The internal process number corresponding to the DCServer)
Scope(format is "module_submodule". default, all module) ://enter
Debug level as following:
0, None;
1, Error.
2, Error and Warning.
3, Error Warning and Info.
Please select level : 3
Debug output orient as following:
0, Standard output.
1, file.
2, share memory.
3, EmfExamDm.
Please select orient : 1
Setting succeeded!
After several operations resulting in the DC Server fault, stop the debug switch.
iMAP>setdbg
Process ID : 148
Scope(format is "module_submodule". default, all module) :
Debug level as following:
0, Null;
1, Error.
2, Error and Warning.
3, Error Warning and Info.
Please select level : 0
Debug output orient as following:
0, Standard output.
1, file.
2, share memory.
3, EmfExamDm.
Please select orient : 0
Setting succeeded!
Obtain the debug information about the DCServer process generated under $n2000/server/debug.
3. The information generated from the first method is less and easier for analysis, so the Method 1is normally used to identify general problems. The second method can generate more information, so it is more complicated for analysis, and often used to identify difficult problems.
Root Cause
In the event of some unpredictable errors during the device operation in the DC Server, such as upgrade failure or patching failure, you can turn on the debug switch in the DC Server process to collect the debug information to identify the cause of the fault.
Suggestions
Null
More related:Introduction to MSTP_Prelude_Overview and History
Thursday, June 8, 2017
NE datacollector in U2000 V1R1 does not working
Issue Description
we are U2000
Version : U2000V1R1C00CP311 to manage Huawei OSN3500 and OSN7500 , and we found
that the NE Datacollector Does not workingThe problem phenomenon as follow ( we have 2 problems ) :
1. After select the NE Datacollector from the OSN function tree , we could not login the the OSN NE in the NE data collector as showed in the b/m print screen
2. After select the NE datacollector from OSN
Function tree, we couldn't find Huawei OSN NE in the Datacollector ( OSN NE
not exist to select Login ) .
Alarm Information
Null
Handling Process
1. check if this problem in one NE or all NEs over
the U2000 .
2. check the U2000 System monitor process (espcially : neproxy process ) .
3. get these logs and sent it to GTAC :
* D:/U2000/server/tools/datacollector/dbfile/Datacollector.db
* D:/U2000/Client/Tools/neinfo.xml
4. check the Set Login account and check the Operated and fixed Users .
5. Check the Upper limit of creation from the datacollector logs if it reach to be 50 (the max ) let us use the temp solution till upgrade the U2000 version to be U2000 V1R2C01SPC100
2. check the U2000 System monitor process (espcially : neproxy process ) .
3. get these logs and sent it to GTAC :
* D:/U2000/server/tools/datacollector/dbfile/Datacollector.db
* D:/U2000/Client/Tools/neinfo.xml
4. check the Set Login account and check the Operated and fixed Users .
5. Check the Upper limit of creation from the datacollector logs if it reach to be 50 (the max ) let us use the temp solution till upgrade the U2000 version to be U2000 V1R2C01SPC100
Root Cause
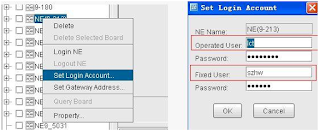
For Problem # 1This problem is due to when your user login, other user resave it, then make this user logout.
Pls check NE--->set login Account, and check whether there has the same user set in this table, if yes, pls change fixed user to other login user. See following picture:
For Porblem # 2 : According to the Logs of the Datacollector we find that :
we find that : the creation NEs of Datacollector is
already reach the upper limit 50
so we need to upgrade current U2000 version to be U2000 V1R2C01SPC100 or use Temp solution as follow :
we can use the new (Datacollector.db) which supprot more 50 NE and replace the new (Datacollector.db) file in path
so we need to upgrade current U2000 version to be U2000 V1R2C01SPC100 or use Temp solution as follow :
we can use the new (Datacollector.db) which supprot more 50 NE and replace the new (Datacollector.db) file in path
Suggestions
1. check all the
U2000 system monitor .2. check the Set Login account in the Datacollector .
3. Use the Temp solution (use the new (Datacollector.db)) if you cannot upgrade the U2000 to be: U2000 V1R2C01SPC100
4. U2000 V1R2C01SPC100 of Higher version solves this problem.
Wednesday, June 7, 2017
missing comopent and instance in U2000 can find the Ethernet trails E-line service
Issue Description
in XXX network there are RTN 900 NE SW version: V100R002C00SPC200 and U2000 version: V1R5C00SPC600
when try to create E-line service by using trails, didnt find it in U2000 although U2000 license support it.
when try to create E-line service by using trails, didnt find it in U2000 although U2000 license support it.
Alarm Information
None
Handling Process
handling the problem as
below :1. check that component (Nativeeth Service Management) in MSuite , didn't found
2. add this component
3. add an instance (NML_VALN)
4. check the U2000 now it OK
Check the components(Nativeeth Service Management) in MSuite and find it is missing, so we should add it to solve the problem.
Suggestions
If you didn’t find the E-Line trail in U2000 and you have
the license of this feature; check the MSuite component (Nativeeth Service
Management) if not found add it.
More related:
Non-universal GEM template and Priority parameters
MA5600T Series LACP Configuration
Subscribe to:
Posts (Atom)